| [1] | A company that provides airport car parking has a web site
where customers select a car park and pay to park their car while on
holiday. The company has purchased a list of email addresses of people
who have recently booked flights. Briefly describe how the company could use these email addresses to sell more car parking spaces and possible benefits for the company of using email in this way. |
[3] | |
|
|||
| [2] | Home computers often store large amounts of data, such as
photographs, videos and personal files on hard disc. As a result of a
disaster such as a house fire or flood the hard disc could be damaged
and the data lost. Describe a suitable strategy for backing up the data and briefly describe how the data may be restored.
|
[4] | |
|
|||
| [3] | Briefly describe the main function of the following components of a computer: | ||
| (a) | control unit; | [1] | |
|
|||
| (b) | arithmetic and logic unit; | [1] | |
|
|||
| (c) | register; | [1] | |
|
|||
| (d) | bus. | [1] | |
|
|||
| [4] | Smash Hits is a successful DVD rental shop with increasing customer numbers. Smash Hits currently store the details about DVDs, customers and rentals on paper which is kept in files behind the counter. It is becoming difficult to find the paperwork for a particular DVD, customer or rental. | ||
| (a) | Briefly describe two other possible problems with the current paper-based system. | [2] | |
|
|||
| (b) | The owner of Smash Hits has purchased a computerised database system. Describe how this system could solve the problems described above. | ||
|
|||
| Also describe a useful report that the new system might produce. | [3] | ||
|
|||
| (c) | Smash Hits will be storing additional customer information such as bank details in the new computerised database system. Describe three ways in which the Data Protection Act will apply to the data stored by Smash Hits. | [3] | |
|
|||
| [5] | Verification checks are carried out on student data stored on a computer at a college. Briefly describe when verification checks would be carried out on the student data and explain the purpose of verification. | [2] | |
|
|||
| [6] | Many people, including children, benefit from using the Internet to make new friends in chat rooms as well as exchanging ideas in forums. | ||
| Discuss the benefits and drawbacks of using the Internet for these purposes. | [6] | ||
|
|||
| [7](a) | Describe in detail the role of the operating system in managing the resources of a computer. | [5] | |
|
|||
| (b)(i) | A computer's hard disc can become fragmented. Explain the term fragmentation and briefly describe the effect that fragmentation will have on disc access. | [2] | |
|
|||
| (ii) | Describe what happens during de-fragmentation. | [1] | |
|
|||
| [8] | Computer files can be organised in serial or sequential order. | ||
| (a) | Briefly describe how records are added to: | ||
| (i) | a serial file; | [1] | |
|
|||
| (ii) | a sequential file. | [2] | |
|
|||
| (b) | Computer files can contain fixed length or variable length records. Describe the difference between fixed and variable length records. | [4] | |
|
|||
| [9] | Below is an incomplete algorithm intended to determine the largest of three integers. Line 12 is incomplete. | ||
| 1 repeat | |||
| 2 input Number1 | |||
| 3 until ( Number1 is an integer ) | |||
| 4 repeat | |||
| 5 input Number2 | |||
| 6 until ( Number2 is an integer ) | |||
| 7 repeat | |||
| 8 input Number3 | |||
| 9 until ( Number3 is an integer ) | |||
| 10 set Biggest = Number1 | |||
| 11 if Number2 > Biggest then Biggest = Number 2 | |||
| 12 if Number3 | |||
| 13 output Biggest | |||
| (a) | Explain the purpose of the repeat - until loop shown below. | [2] | |
| 1 repeat | |||
| 2 input Number1 | |||
| 3 until ( Number1 is an integer ) | |||
|
|||
| (b) | Complete line 12 of the algorithm. | [1] | |
|
|||
| [10] | "In the future we will be able to talk to computers and keyboards will not be required". | ||
| Discuss the advantages and disadvantages of speech input. | [6] | ||
|
|||
| [11] | Briefly describe the most suitable use for each of the following protocols: | ||
| (a) | FTP ( File Transfer Protocol ): | [1] | |
|
|||
| (b) | HTTP ( Hypertext Transfer Protocol ): | [1] | |
|
|||
| (c) | SMTP ( Simple Mail Transfer Protocol ): | [1] | |
|
|||
| [12] | Below is an algorithm. | ||
| Algorithm FindTotal | |||
| Num1 is integer {number input by user} | |||
| Num2 is integer {number input by user} | |||
| declare subprocedure AddTwoNum {procedure to find the total of two integer and output the answer} | |||
| Total is integer {variable to store the answer} | |||
| start | |||
| set Total = Num1 + Num2 | |||
| output "the total is ", Total | |||
| end | |||
| startmainprog | |||
| output "type in first number" | |||
| input Num1 | |||
| output "type in second number" | |||
| input Num2 | |||
| call AddTwoNum | |||
| endmainprog | |||
| (a) | Write down one example of annotation from the algorithm above and explain why annotation is used in computer programs. | [2] | |
|
|||
| (b) | Using examples from the above algorithm, describe the difference between local and global variables. | [4] | |
|
|||
| [13] | In a computer different data types use different amounts of memory. | ||
| (a) | Give an example of data that could sensibly be stored as | [2] | |
| (i) | integer data type | ||
|
|||
| (ii) | real data type | ||
|
|||
| (b) | Using an example of data that could sensibly be stored in each data type, compare the amount of memory required to store a character with the amount of memory required to store a string. | [4] | |
|
|||
| [14] | A bank has an internet site and an intranet. | ||
| (a) | Give two examples of information which might sensibly be found on their internet site. | [2] | |
|
|||
| (b) | Give two examples of information which should only be found on their intranet, explaining why this information should not be on the internet? | [4] | |
|
|||
| [15] | Explain how a linear search algorithm would determine whether an item called SearchValue is present in an array called SearchArray. | [3] | |
|
|||
| [16] | A water company monitors the amount of water in its reservoirs and the amount of rain falling. During a water shortage, the company is able to ban its customers from using hosepipes. In extreme conditions the water company has the power to ration the water supply to its customers, by turning off the supply for several hours per day. | ||
| The algorithm used by the company is shown below: | |||
| Statement | |||
| 1 input ReservoirLevel | |||
| 2 input DaysSinceLastRain | |||
| 3 if (( ReservoirLevel < 20% ) OR | |||
| (( ReservoirLevel < 30% ) AND ( DaysSinceLastRain > 21 ))) | |||
| 4 then output "Rationing" | |||
| 5 else if (( ReservoirLevel < 40% ) AND ( DaysSinceLastRain > 14)) | |||
| 6 then output "Hosepipe ban" | |||
| 7 else output "Normal" | |||
| (a) | State what the output will be when the inputs are: | ||
| (i) | Reservoir level = 35% Days since last rain = 16 | [1] | |
|
|||
| (ii) | Reservoir level = 32% Days since last rain = 12 | [1] | |
|
|||
| (iii) | Reservoir level = 15% Days since last rain = 12 | [1] | |
|
|||
| (iv) | Reservoir level = 28% Days since last rain = 25 | [1] | |
|
|||
| (b) | The water company decides to change statement 3 so it becomes: | ||
| 3 if (( ReservoirLevel < 20% ) OR | |||
| (( ReservoirLevel < 25% ) AND ( DaysSinceLastRain > 21))) | |||
| (i) | State which part or parts of (a)(i) to (a)(iv) now gives a different output. | [1] | |
|
|||
| (ii) | What will the new output or outputs be? | [1] | |
|
|||
| [17] | When a student applies to do a course at a particular music college, he or she completes an application form and asks someone ( a referee ) to supply a reference to the College. When the College receives the application and reference, its admissions tutor checks on a national database any musical examination results claimed by the student. The student is then interviewed and if successful he or she is added to the list of students approved for entry to the College. | ||
| The situation described is shown in the data flow diagram below: | |||
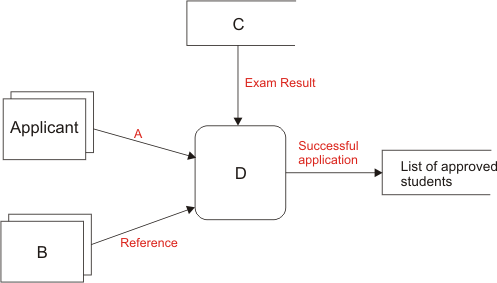 |
|||
| (a) | Why do systems analysts find data flow diagrams very useful? | [1] | |
|
|||
| (b) | What type of object dose the rounded box represent? | [1] | |
|
|||
| (c) | Draw the shape used in the diagram to represent an external entity. | [1] | |
|
|
|||
| (d) | Give a suitable name for the object shown as A in the diagram. | [1] | |
|
|||
| (e) | Give a suitable name for the object shown as B in the diagram. | [1] | |
|
|||
| (f) | Give a suitable name for the object shown as C in the diagram. | [1] | |
|
|||
| (g) | Give a suitable name for the object shown as D in the diagram. | [1] | |
|
|||
| [18] | A large government department, having decided to update one of its computer systems, has carried out a feasibility study and has awarded the contract to update the system to a company called Cymrix. Staff at Cymrix will now analyse the current system and design a new system. | ||
| Describe in detail the activities carried out during the feasibility study | |||
| Describe in detail the activities that will be carried out during the analysis and design stages. | |||
| Describe in detail the different methods of changeover that could be considered by Cymrix. | [12] | ||
|
|||