| 1.(a) | Describe what is meant by each of the following terms, giving one example in each case: | |||||||||||||||||
| (i) | syntax error; | [2] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | logical error. | [2] | ||||||||||||||||
|
||||||||||||||||||
| (b) | Give one reason why it is usually easy to discover a syntax error. | [1] | ||||||||||||||||
|
||||||||||||||||||
| 2(a) | An integrated package contains word processing and spreadsheet facilities. Two features of the integrated package are editing capabilities and mail-merge. | |||||||||||||||||
| (i) | Give an example to show how editing capabilities could be used. | [1] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | Using an example, show how a mail-merge operation could link the word processing and spreadsheet facilities together. | [2] | ||||||||||||||||
|
||||||||||||||||||
| (iii) | Describe one advantage of having a programming facility within the package. | [1] | ||||||||||||||||
|
||||||||||||||||||
| (b) | The developers of this integrated
package have tried to ensure that it has a well-designed and
"user-friendly" human-computer interface (HCI).
Describe three features of a well-designed HCI |
[3] | ||||||||||||||||
|
||||||||||||||||||
| 3(a) | A linear search is used to search for one particular number in a large set of ordered numbers. | |||||||||||||||||
| (i) | Name an alternative search method which will usually find the number more quickly than a linear search. | [1] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | Explain how this alternative search works, using a diagram if you so wish. | [3] | ||||||||||||||||
|
||||||||||||||||||
| (b) | State a circumstance in which the linear search is the most suitable method. | [1] | ||||||||||||||||
|
||||||||||||||||||
| 4(a)(i) | Give an example of some data which could be conveniently stored in a record, but which could not be stored in a two-dimensional array. | [1] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | Explain why the data could not be stored in a two-dimensional array. | [1] | ||||||||||||||||
|
||||||||||||||||||
| (b) | Give an example of some data which could conveniently be stored in a two-dimensional array. | [2] | ||||||||||||||||
|
||||||||||||||||||
| 5(a) | A certain programming language has excellent record-handling and file-handling capabilities. What type of application might this language be suitable for? | [1] | ||||||||||||||||
|
||||||||||||||||||
| (b) | Another programming language handles complex calculations very well. What type of application might this language be suitable for? | [1] | ||||||||||||||||
|
||||||||||||||||||
| (c) | Another programming language allows different fonts and layouts to be used and allows access by a number of browsers. What is the main use of this type of language? | [1] | ||||||||||||||||
|
||||||||||||||||||
| 6. | In each case, name a suitable data type for the storage of the following data: | |||||||||||||||||
| (i) | a person's surname, for example Evans | [1] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | the first initial of a person's name, for example J | [1] | ||||||||||||||||
|
||||||||||||||||||
| (iii) | a person's age in complete years, for example 27 | [1] | ||||||||||||||||
|
||||||||||||||||||
| (iv) | a person's height in metres, for example 1.62 | [1] | ||||||||||||||||
|
||||||||||||||||||
| (v) | whether a person is left-handed, for example TRUE | [1] | ||||||||||||||||
|
||||||||||||||||||
| 7(a) | The term rogue value is often used in connection with data input to a computer program. State an application which could use a rogue value and give an example of a set of data for this application, clearly indicating the rogue value. | [2] | ||||||||||||||||
|
||||||||||||||||||
| (b) | Explain what is meant by the scope of a variable in a computer program. | [1] | ||||||||||||||||
|
||||||||||||||||||
| 8. | A software house is developing a computer system to handle emergency calls to a city's ambulance service. The software development team uses various methods to ensure that the software is of very high quality. | |||||||||||||||||
| (i) | Why is it very important that this computer system is of very high quality? | [1] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | I Explain what is meant by self-documenting code. | [1] | ||||||||||||||||
|
||||||||||||||||||
| II Give one reason why the development team might use self-documenting code. | [1] | |||||||||||||||||
|
||||||||||||||||||
| (iii) | Give three reasons why the development team might use standard modules. | [3] | ||||||||||||||||
|
||||||||||||||||||
| (iv) | Explain why careful version control is important. | [1] | ||||||||||||||||
|
||||||||||||||||||
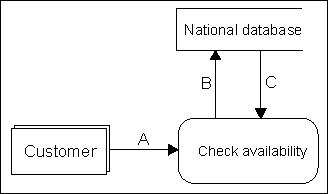
| 9. | A specialist car dealer supplies
classic cars to its customers. The dealer finds suitable cars by searching
a national database.
The situation is shown in the diagram below: |
|||||||||||||||||
|
|
||||||||||||||||||
| (i) | Write down the name for this type of diagram. | [1] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | What type of object does a shadow rectangle (for instance Customer in the above diagram) represent? | [1] | ||||||||||||||||
|
||||||||||||||||||
| (iii) | What type of object does a rounded rectangle (for instance Check availability in the above diagram) represent? | [1] | ||||||||||||||||
|
||||||||||||||||||
| (iv) | Give a suitable name for the object shown as A in the diagram. | [1] | ||||||||||||||||
|
||||||||||||||||||
| (v) | Give a suitable name for the object shown as B in the diagram. | [1] | ||||||||||||||||
|
||||||||||||||||||
| (vi) | Give a suitable name for the object shown as C in the diagram. | [1] | ||||||||||||||||
|
||||||||||||||||||
| 10. | A sophisticated burglar alarm in an
art gallery has a backup electricity supply which normally starts working
within a second or two of the main electricity supply failing.
The burglar alarm rings a loud bell if an intruder is detected inside the building. Since security is of great importance, the alarm also sounds if the main electricity supply fails and is not restored within five seconds. (You may assume that the bell itself has its own unbreakable electricity supply.) Inputs to the control system are: intruder main-electricity-supply time-since-main-electricity-failed The algorithm used is shown below. |
|||||||||||||||||
Statement
|
||||||||||||||||||
| (a) | State what will happen when the three inputs are: | |||||||||||||||||
|
[3] | |||||||||||||||||
|
||||||||||||||||||
| (b) | The burglar alarm would fail to work correctly if the word AND in statement 5 was replaced with the word OR. Describe what would go wrong. | [1] | ||||||||||||||||
|
||||||||||||||||||
| 11. |
In the following question, additional credit (up to
3 marks) will be given if your answer demonstrates skill in written
communication.
Apex Bikes sells a large range of bicycles, from children's bicycles to professional racing bicycles. Apex sells bicycles from the shop and also orders them for customers. Currently, the shop does not use a computerised system. Apex's owner would like to introduce a computer system to show customers what is available and also for ordering bicycles from suppliers. Imagine you are employed as a systems analyst by the owner of Apex. Five steps you will need to carry out are the requirements analysis, the requirements specification, the design of the new system, the selection of suitable hardware and the selection of suitable software. Describe in detail how you would carry out the five steps shown in italics in the above paragraph. |
[8 +3] | ||||||||||||||||
|
The requirements
analysis will involve investigating how the present system works in the
shop in order to find out what the main problems are. The investigation
will involve spending some time observing operations in the shop, and
may involve interviews with the staff or questionnaires which I will ask
them to fill in.
The requirement specifications can then be produced. This will be a list of the objectives which the new system must meet, and what it needs to be able to do. There may also be criteria suggested by which the success of the new system can be measured. The new system can then be designed. The design will be subject to restraints that the management of the shop may impose - these may involve financial limits or time limits when the new system must be installed by. Selection of suitable hardware will involve the selection of the computers, any networking as well as specialist peripherals which may be needed such as bar-code readers. Software will also need to be selected for installing on the computers. These programs may be bought from software suppliers, or written and coded by programmers to the specifications which the shop needs.
|
||||||||||||||||||