| 1. | A public library owns thousands of books, CDs and other items. Each item is given a unique identification code made up of two letters and four digits, for instance GR2351. Validation is used on the codes. | |
| (i) | What is the purpose of validation? | [1] |
To
test if the data is reasonable before it is processed. |
||
| (ii) | Describe two types of validation which might be applied to this code, stating in each case how it might be applied. | [4] |
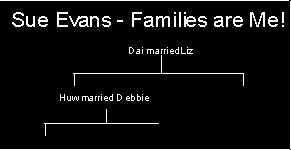
| 2. | Sue Evans runs a small business in which she
tries to trace people's family histories.
Customers are asked about their parents, grandparents and other relatives and then Sue refers to census information, parish records and other documents. She also has a network of contacts around the world whom she telephones: these are people in a similar line of business who can help her in the search for information. Currently, Sue does not use a computer. For each customer, she creates a paper file which she may add to over several months. Before presenting all her findings to the customer, she produces an attractive typed report detailing all the information gathered, and draws a decorative family tree diagram. Sometimes she photocopies valuable and attractive documents and includes them in the final file. |
|
| (i) | Explain why this paper-based system will cause Sue some difficulties. | [2] |
|
||
| (ii) | Sue has now obtained some information about a computer system consisting of a personal computer and specialist software which may be able to help her run the business more efficiently. | |
| I | Informaton is required about each relative of the customer. State two different items of information which the system could usefully store about each relative. | [2] |
|
||
| II | Describe two features that this specialist software would need. | [2] |
|
Describe two special hardware items which might also be useful for Sue, with a reason in each case. | [2] |
|
||
| 3(a) | Using a diagram, explain in detail each of the following file structures. In each case, also describe how a new record is inserted: | |
| (i) | serial access file | |
Records are stored in the order in which they occur. A new record is added onto the end. |
||
| (ii) | sequential access file | [3] |
Records
are stored in sorted order (of a key field).
A new record would need to be 'inserted' in the file at the right place. |
||
| (b) | Describe an application of each of the following file structures, making it clear in each case why the file structure is appropriate in this case. | [2] |
A
transaction file for a mail-order business may be stored as a serial
access file. As orders are received they are placed on the file and
processed in the order in which they are received. |
||
| (ii) | sequential access file | [2] |
|
An
exam board may store data sorted in order of school name so that when
certificates are printed out, all the certificates from one school will be
together. |
||
| 4 | A certain computer uses a word length of 32 bits. | |
| (i) | What is meant by the term word in this context? | [1] |
The
amount of data the computer can process at a time. |
||
| (ii) | What advantage is derived from using a long word length? | [1] |
The
computer will be able to process data faster so programs will execute
quicker. |
||
| 5.(a) | Explain what is meant by the term database. | |
|
A
collection of related files (tables). |
||
| (b)(i) | Give two reasons why data duplication is often considered very undesirable. | [2] |
|
||
| (ii) | Describe how a database system can avoid duplication. | [1] |
Store
all the data in a central database and use a network to allow users to
access it from a number of workstations. All data would only be stored
once. |
||
| 6. | The Megahire car hire company has a large number of customers (mainly other firms) who hire cars regularly. Megahire uses a large computer system to run its business. It uses batch processing and interactive systems for different applications. | |
| (i) | Describe what is meant by batch processing and describe an application where Megahire might sensibly use a batch processing system, amking it clear why a batch processing system is suitable in this case. | |
Collecting
similar jobs to run them together.
The firm might run their payroll system using batch processing. There is no immediacy so it can be run at off-peak times. There is no need for human intervention during processing. |
||
| (ii) | Describe what is meant by an interactive system and describe an application where Megahire might sensibly use an interactive system, making it clear why an interactive system is suitable in this case. | [3] |
The
car hire booking system would use an interactive system as there is a need for human
interaction when bookings are made or cancelled. |
||
| 7(a) | Describe three functions of the operating system of a personal computer. | [3] |
|
|
|
| (b) | A number of hand-held computers now use handwriting recognition as a means of input. Describe one advantage and one disadvantage of this input method. | [2] |
Advantage
: There is no need for paper.
Disadvantage : There may be accuracy problems if someone's handwriting is not very clear. |
||
| 8. | Chris Williams is responsible for computer security and computer-related ethical and legal issues for West Wales Bank(WWB). | |
| (i) | One particular concern is the possible theft of valuable data held in the Bank's computer system. Describe three methods by which the risk of theft can be reduced. | [3] |
|
||
| (ii) | Another concern is the accidental loss of data. Describe one method by which the risk of accidental loss can be reduced. | [1] |
Backups
of all current data should be made. |
||
| (iii) | Chris has to be careful that the Bank complies with all the computer related legislation, such as the Data Protection Act. Describe three ways in which the Data Protection Act will apply to WWB. | [3] |
|
||
| (iv) | There are concerns in WWB about computer-related health and safety issues. Describe the likely nature of the concerns and how the problem might be eased. | [2] |
|
||
| (v) | There are also concerns in WWB about the possibility of staff being made redundant. Describe the likely nature of the concerns and how the problem might be eased. | |
|
||
| 9.(a) | Describe, with the aid of a diagram, the main features of each of the following network types: | |
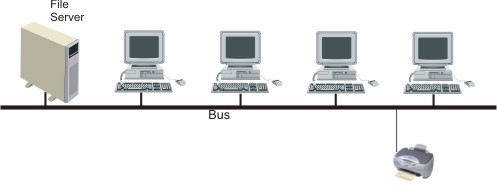
| (i) | bus network; | [2] |
All
computers are linked along one 'bus' - a cable which they share to
transmit data.
|
||
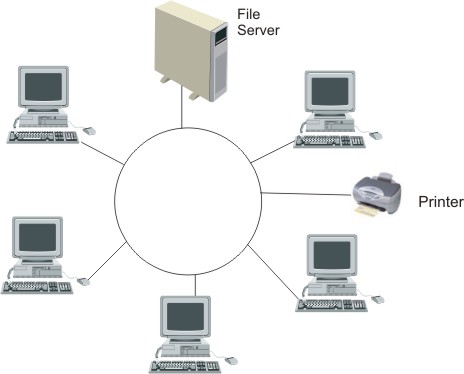
| (ii) | token ring network. | [3] |
All
computers are linked in a loop.
Data is transmitted round the ring as a 'token' with information about its destination. This token is then collected by the receiving computer.
|
||
| (b) | Computer networks tend to be particularly prone to attack by computer hackers. Give one reason why this is the case. | [1] |
It
is easy for a hacker to hide his identity and access data on a computer
system often without even being detected. |
||
| (c) | Peripherals such as printers often use handshaking in communicating with the computer. Give an outline example of handshaking as applied to the use of a printer. | [3] |
|
||
| 10. | In the following question, additional credit (3 marks) will be gained if your answer
demonstrates skill in written communication.
The students and staff in a college make extensive use of email and the internet, and also the college's own intranet. Describe in detail how email, the internet and the intranet would be useful to both staff and students. In your answer, you should consider the types of information being stored and communicated, and the purpose of the storage/communication. |
[8+3] |
Email is a
method of communicating between two computer users and could be used by
students to request help from staff about any problems or to send them
completed pieces of work. The staff could quickly respond to any
assistance or send back assessed and corrected work to the student.
The Internet could be used by students to research and retrieve information to help with assignments or request information using bulletin boards or news groups. Students could also publish their completed research on a website which could then be accessed by other students. Staff could also set up websites to advertise the college and the courses it offers to try to attract prospective students. The college intranet could be used to store frequently needed information or pages of information about the college eg course timetables, plan of the college site. Students could also use the intranet for internal emails.
|
||