| [1] | A travel agency uses a word processing package to produce
letters that are sent to customers. Two features of the word processing
package that are regularly used are:
(i) header/footer (ii) print preview |
|
| Describe each of the features named above, and give an example of how each feature could be useful to the agency. | [4] | |
|
||
| [2] | One method of transferring electronically stored programs or data onto a Personal Computer is from a floppy disc. State three other methods of transferring such programs or data onto a Personal Computer. | [3] |
|
||
| [3] | A hairdresser's salon receives bookings from customers
over the telephone. They record the customer's name, address, date and
time of appointment and the stylist required. This information is input into
a database. |
|
| (i) | Explain the term database. | [1] |
|
||
| (ii) | Describe two benefits for the salon manager of using a database to store information about each booking. | [2] |
|
||
| (iii) | Give two reasons why data duplication is undesirable in a database. | [2] |
|
||
| [4](a) | Draw diagrams to show the difference between a ring network and a bus network. | [2] |
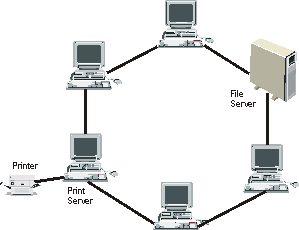 Ring
Network Ring
Network
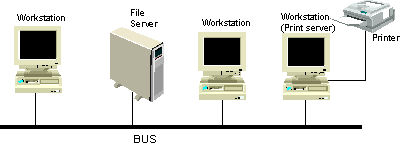 Bus
Network Bus
Network
|
||
| (b) | Explain the difference between a local area network (LAN) and a wide area network (WAN). | [1] |
|
||
| (c) | What is an interface between a peripheral and a computer? | [1] |
|
||
| [5] | When a student enrols at a college their personal details
are entered into a database. The data is validated
and verified. |
|
| (i) | Explain the difference between data verification and data validation. | [2] |
|
||
| (ii) | (I) Type check is one method of data validation. Using an example, explain the term type check. | [1] |
|
||
| (II) Give an example of invalid data for a type check that may be carried out on a student's personal details. | [1] | |
|
||
| [6] | A common method of input to a computer system is the keyboard. Speech is an alternative method of input. Describe a suitable application of speech input, giving two benefits and two drawbacks. | [5] |
|
||
| [7](a) | Name an application where real time processing is necessary. Explain how real time processing operates in this case and give one reason why real time processing is necessary. | [3] |
|
||
| (b) | Explain what is meant by the term batch processing, and name an application where batch processing is appropriate. | [2] |
|
||
| (c) | A school network makes use of spooling. Explain in detail how spooling is used for printing. | [3] |
|
||
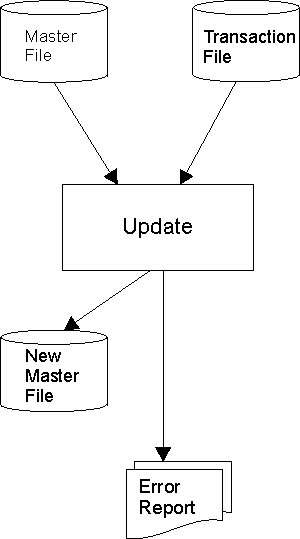
| [8](a) | Explain how a record is added to: |
|
| (i) | a serial file | [1] |
|
||
| (ii) | a sequential file | [2] |
|
||
| (b) | Draw a detailed diagram which clearly shows how a master file is updated using a transaction file. | [3] |
|
||
| [9] | SuperSure is an insurance
company with offices throughout the country. Staff have access to
customers' information. They logon to the company's computer system
using usernames and passwords. |
|
| (i) | For security reasons, staff must change their passwords every month. Describe two guidelines the insurance company should provide to staff when they create their new passwords. | [2] |
|
||
| (ii) | The company suspects that some staff are benefiting
illegally from having access to customers' information. |
|
| (I) The company has a code of conduct with which all employees are required to comply. Explain how this code of conduct may reduce such illegal activity. | [1] | |
|
||
| (II) Apart from passwords and a code of conduct, describe two other measures that the company might adopt to try to prevent the computer staff taking part in such illegal activities. | [2] | |
|
||
| (iii) | The company complies with the Data Protection Act by ensuring that customers' information is held securely. Describe three other ways in which the company must operate in order to comply with the Data Protection Act. | [3] |
|
||
| [10](a) | A computer can have a word length of 32 bits. What is meant by the term word in this context? | [1] |
|
||
| (b) | A computer manufacturer produces several different computers. One computer has a word length of 16 bits and another has a word length of 32 bits. Explain why the computer with a 32 bit word length may process data faster. | [1] |
|
||
| [11] | In the following question,
additional credit (up to 3 marks) will be given if your answer
demonstrates skill in written communication.
|
|
| A company that writes computer games employs a team of
programmers to write a new game. The programmers will be provided with
the necessary hardware and software and will work from home.
Describe how the programmers could make use of email and the Internet. Describe the benefits for the programmers and the benefits for the company of the programmers working from home. |
[8+3] | |
The programmers can keep in touch by sending each
other emails, giving and receiving instructions. They will be working on
different sections of the program and can attach files containing sections
of code to each other. Sometimes subroutines can be called by many other
lines in the program.
The programmers can use the Internet for research, for help if they are experiencing problems or they can download previously coded subroutines written and tested by other programmers. The benefits for the programmers include being able to choose when they work. Time and money are also saved because they do not have to travel to work. A better working atmosphere may exist in the home rather than in a noisy and busy office environment. The company would not have to provide office space for the programmers or provide other facilities such as toilets, canteen, or car parking space. This should save the company money, and they would also save money on heating and lighting bills.
|
||