| [1] |
A low cost airline sends emails to customers advertising
flights for sale. |
|
| (a) |
Give two reasons, apart from
speed of delivery and cost, why the airline may prefer to use email for
this communication instead of using conventional post. |
[2] |
|
- using an address list, the same email can
be sent to a large number of people
- multimedia attachments such as video clips
can be sent
|
|
| (b) |
Describe one problem that may arise from using email in
this way. |
[1] |
|
| |
| |
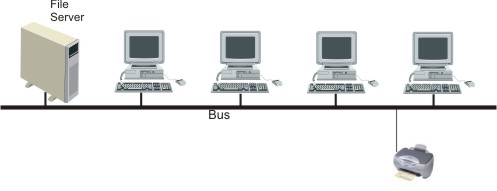
| 2.(a) |
Draw a diagram of a bus network. |
[1] |
|
| |
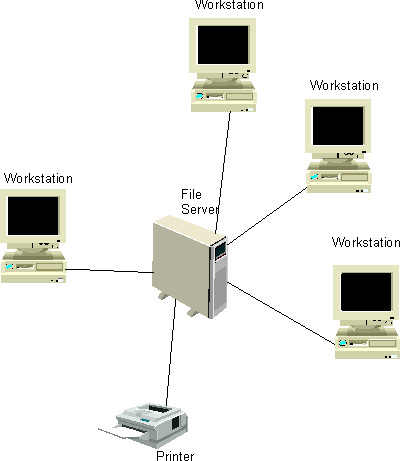
| (b) |
Draw a diagram of a star network. |
[1] |
|
- xxx
| |
| (c) |
Give one advantage of
using a star network rather than a bus network. |
[1] |
|
- reliable - if one workstation goes down,
the rest of the network is unaffected.
| |
| (d) |
Describe two advantages
of network computers compared with standalone computers. |
[2] |
|
- hardware can be shared eg. printer
- workstations on the network can
communicate (send emails or files)
|
|
|
| |
| 3. |
Many cars are now fitted with satellite navigation
systems. The car's destination is input and the driving directions are
output. |
|
| (a) |
One method of output is a screen display. looking at
the screen while driving would be distracting for the driver. What other
method of output would be more suitable? |
[1] |
|
- speech synthesis (voice output)
| |
| (b) |
Explain why voice input would be a suitable method
of input for this device. |
[1] |
|
- the driver does not have to use hands, or
look at the device and can carry on driving safely.
| |
| (c) |
Describe two situations
where voice input may not be recognised by the device. |
[2] |
|
- local regional accents may not be
recognised
- illness such as a cold may cause a voice
to be unclear
| |
|
| |
| 4. |
A secondary school has a file server with a 500
gigabyte hard disc. |
|
| (a) |
Describe in detail a
suitable strategy for backing up the data stored on the file server. |
[2] |
|
- Use another high-capacity external hard
disc drive...
- ...and copy the contents of the current
drive onto it every night.
| |
| (b) |
Describe in detail a
suitable strategy for restoring this data after a failure. |
[2] |
|
- Store the backup drive off-site, away from
hazards
- Copy the contents back onto the original
drive.
| |
|
| |
| 5. |
An optician collects customer's details during their
first visit. These details are stored on paper in files. |
|
| The number of customers is increasing and the
optician finds that amending customer details is extremely time
consuming. Describe two other possible
problems with the current paper-based system and describe how a
computerised database system could solve these
problems. |
[4] |
|
- Searching for a client's detail takes a
long time....
- ...a computerised database has high-speed
search facilities (queries)
- Clients details are getting lost...
- ...the database can be backed up regularly
to prevent data loss.
| |
|
| |
| 6. |
Validation checks are carried out on customer data
entered into a computer at a car rental company. |
|
| (a) |
What is the purpose of validation checks? |
[1] |
|
- checks that the data is reasonable /
sensible
| |
| (b) |
One item of data being entered is the age of the car
driver. Name a suitable validation check and describe how this check
would detect an invalid age being entered. |
[2] |
|
- A range check could be used ...
- ...to check the age is between defined
limits eg between 18 and 80
| |
|
| |
| 7. |
The Conifer Hotels group has hundreds of hotels
throughout the world. Guests of Conifer Hotels have loyalty cards that
earn points for every stay at a participating hotel. Guests can access
their loyalty card accounts on-line using the Internet. They are able to
view statements and use points to claim free hotel nights. These
accounts could be subject to malicious or accidental
damage. |
|
| (a) (i) |
Describe what is meant by the term malicious
damage and explain how Conifer hotels could prevent malicious
damage to the data stored in these accounts. |
[2] |
|
- Intentional altering or deleting of data
Eg by hackers
- Use usernames and passwords to access the
data
| |
| (ii) |
Describe what is meant by the term accidental
damage and explain how Conifer Hotels could prevent
accidental damage to the data stored in these accounts. |
[2] |
|
- Unintentional alteration of data by
mistake
- Make important data read-only.
| |
| (b) |
Conifer Hotels comply with the Data Protection Act
by ensuring that guests data is up to date and accurate, held securely
and held for no longer than necessary. Describe three
other ways in which Conifer Hotels must operate in order to
comply with the Data Protection Act. |
[3] |
|
- Data must be obtained fairly and lawfully
- Data must only be used for the stated
purpose
- They must allow customers to check their
personal data to see if it is correct, and change it if it is not.
| |
|
| |
| 8. (a) |
An operating system provides an interface between
the hardware and the user and manages system resources. |
|
| (i) |
Describe three
functions of an operating system from a user's point of view. |
[3] |
|
- Loads and runs programs
- Maintains security - only allowing
authorised users to have access to the computer system.
- Allows users to copy or delete files and
folders.
| |
| (ii) |
Name three resources
which an operating system would manage. |
[3] |
|
- Backing storage devices such as hard
drives/USB memory sticks
- Memory (RAM)
- Input and output from input or output
devices such as keyboard/mouse
| |
| (b) |
A theatre sells tickets using real time transaction
processing. Describe how real time transaction processing works in this
case and explain why it is the most suitable mode of operation |
[2] |
|
- As soon as the computer receives the data,
it is processed and data is updated.
- Prevents double-booking of tickets.
| |
|
| |
| 9. (a) |
Records within a file can be fixed
length or variable length. Describe the
difference between fixed and variable
length records, giving one advantage of
using a variable length record. |
[3] |
|
- Fixed length records - all records are the
same size (number of bytes)
- Variable length - the records are
different sizes, with separators between each field.
- Advantage of variable length - file size
will be smaller so faster to download or transmit files.
| |
| (b) |
A household gas supplier takes readings from
customers' gas meters every three months. The current meter reading for
each customer is stored in a transaction file.
Customer details are stored in a master file. |
|
| (i) |
Why is serial file organisation the most suitable
method for the transaction file? |
[1] |
|
- There is no order and records can be added
to the end of the file as they occur.
| |
| (ii) |
Why is sequential file organisation the most
suitable method for the master file? |
[1] |
|
- The records can be accessed in sorted
order for the update process.
| |
| (iii) |
Explain how the transaction file is used to update
the master file when producing the gas bills. |
[2] |
|
- A new master file is created
- Each transaction record in turn is either
copied to the new file, or used to update the corresponding record
in the master file which is then saved in the new file.
| |
|
| |
| 10. |
Explain what is meant by each of the following
computer terms: |
|
| (a) |
address bus; |
[1] |
|
- The path down which address data is sent
| |
| (b) |
byte; |
[1] |
|
| |
| (c) |
word; |
[1] |
|
- The number of bits that a processor can
process at a time.
| |
| (d) |
disk cache memory. |
[1] |
|
- An area of memory that stores data that
has been read from a hard disc.
| |
|
| |
| 11. |
In the following question,
additional credit ( up to 3 marks) will be given if your answer
demonstrates skill in written communication. |
|
| A computer software company has been asked to
produce a commercial web for a customer. The company employs a team of
software developers who will be provided with the necessary hardware and
software and will work from home and will have access to the company
intranet. |
|
| From the company perspective describe the
benefits of the developers working from home. |
|
| From the developers' perspective describe the drawbacks
of working from home. |
|
| Explain why the software developers would find the company's
intranet useful. |
[8+3] |
|
- The company would not have to provide
office space for the developers and would save money on electricity
bills as they would not have to provide lighting or heating. They
also would save money as they do not need to provide other
facilities such as canteen food, toilets or car parking. The web
project may also be completed faster because the developers could
work in a more relaxed atmosphere in their homes, and work the hours
they want to.
- There may a certain amount of distraction
in the home environment such as small children or pets, and
motivation to do the work may be difficult to achieve. There would
also be a lack of social contact with fellow workers.
- The developers could use the company's
intranet to keep in touch with the latest news and developments of
the company, and they could use it to inform fellow workers about
progress of the web. The intranet could also be used to communicate
with other workers and share ideas about the web project.
| |
| | |
| |