| 1. | Explain the meanings of the terms field, record and file, giving one example to illustrate the three terms. | [5] | ||||||||||||||||
|
||||||||||||||||||
| 2. | John Smith owns a small firm which does gardening work for a number of private individuals and small companies. | |||||||||||||||||
| John works in a variety of ways. For instance, some of his customers employ him for an hour or two per week to do general gardening work; others employ him for certain larger jobs, for instance cutting hedges twice per year; others simply contact him on occasions. John also has arrangements with some customers that he will spend some extra time working for them (at a reduced rate) when he has no other work to do. Some customers are particularly interested in certain plants, and are always interested in any new varieties that become available or any other relevant information. | ||||||||||||||||||
| Sometimes, John does quite large landscaping gardening projects for customers, where he might change the lay-out of a whole garden. | ||||||||||||||||||
| He currently stores information about each customer on one or more paper forms in a folder. In addition to basic information about the customer, each form indicates any particular arrangements or interests of the customer, and records of invoices sent and payments received. | ||||||||||||||||||
| The number of John's customers is growing quite rapidly and he no longer finds this paper system adequate. | ||||||||||||||||||
| John could use a personal computer to solve some of these problems. | ||||||||||||||||||
| (i) | Items of data stored in the system include basic customer data such as name and address. Describe three other relevant items of data which should be stored in the system. | [3] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | Describe, with reasons, the most suitable type of software for this application. | [3] | ||||||||||||||||
|
A relational
database would be the most suitable software. (Details could be kept in two
related tables : Customers and Jobs.)
|
||||||||||||||||||
| (iii) | John has recently acquired a high specification portable ("lap-top") personal computer. Describe how this might be particularly useful to him. | [2] | ||||||||||||||||
|
||||||||||||||||||
| 3(a) | A school holds records of its students in various places, for instance, each form tutor has a record of the student's home address, as does the school office and the head of year. | |||||||||||||||||
| (i) | Give two reasons why this duplication of data is undesirable. | [2] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | How could a database help to solve this problem? | [1] | ||||||||||||||||
Data
is stored only once in a central place accessible from a network.
Different applications could use the database for a number of tasks. |
||||||||||||||||||
| (b) | A school secretary has some health concerns about spending several hours each day using a personal computer. Describe two areas of possible concern. | [2] | ||||||||||||||||
|
||||||||||||||||||
| 4(a) | One method of data validation is the use of a range check. Explain the term range check giving one example which includes both valid and invalid data. | [3] | ||||||||||||||||
It
is a check to see that data lies within a sensible range. For example, a
date - the day should lie in the range 1 to 31.
Valid data - 12 |
||||||||||||||||||
| (b) | Explain what is meant by the term data verification. | [1] | ||||||||||||||||
Checking
for transcription (typing) errors by keying in data twice. The computer
will only accept the data if the two versions are identical.
|
||||||||||||||||||
| 5(a) | Providing a suitable example in each case, describe when it might be sensible to use | [2] | ||||||||||||||||
| (i) | a serial file | |||||||||||||||||
When
data is placed on a file in the order in which it arises. For example,
the orders of a mail order catalogue business may be placed on a serial
file as the orders arrive at the company.
|
||||||||||||||||||
| (ii) | a sequential file | [2] | ||||||||||||||||
A
sequential file is sorted into order of a keyfield. An information
retrieval system (Eg telephone directory file - sorted in order of persons name)
|
||||||||||||||||||
| (b) | Files can have either fixed length or variable length records. | |||||||||||||||||
| (i) | Give one advantage of each type of record. | [2] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | Give one example where it would be appropriate to use variable length records. | [1] | ||||||||||||||||
Where
storage space is minimal eg a computer with a small disc drive.
|
||||||||||||||||||
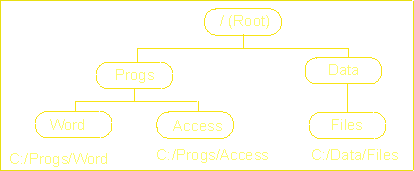
| 6(a) | Files on hard disc are usually stored in a directory with a hierarchical structure. Using a diagram, explain what the term hierarchical structure means in this context. | [2] | ||||||||||||||||
There
is a root which has sub-directories off it. Each of these
sub-directories may themselves have a number of sub-directories and so
on...
The root directory in the diagram has two subdirectories ('Progs' and 'Data') etc...
|
||||||||||||||||||
| (b) | A small firm holds some very valuable data about its customers. Most of these data are held on the hard discs of personal computers in the main office. | |||||||||||||||||
| (i) | Describe one advantage of storing data on a hard disc compared with floppy discs. | |||||||||||||||||
Loading and saving data is much
faster. |
||||||||||||||||||
| (ii) | Describe two disadvantages of storing data on a hard disc compared with floppy disc. | [2] | ||||||||||||||||
|
||||||||||||||||||
| (iii) | Sometimes, data are copied onto floppy discs and deleted off the hard disc. Describe one possible advantage of this approach. | [1] | ||||||||||||||||
It
releases space on the hard disc for other data.
|
||||||||||||||||||
| (iv) | Describe two ways in which data protection legislation might apply to this firm. | [2] |
|
|||||||||||||||
| 7. | A motoring organisation receives many thousands of application forms containing data such as the names, addresses and vehicle details of people wishing to join the organisation. Many staff are employed entering the data into the organisation's computer system. The normal method of entering the data is via the keyboard, but the system manager is experimenting with voice input. | |||||||||||||||||
| (i) | Describe two advantages that voice input would have over the use of a keyboard in these circumstances. | [2] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | Describe three advantages that the use of a keyboard would have over voice input in these circumstances. | [3] | ||||||||||||||||
| ||||||||||||||||||
| (iii) | Describe why an analogue to digital converter is required when voice input is used. | [1] | ||||||||||||||||
|
A microphone is
an analogue device and computers process digital data. An analogue-to-digital will convert the analogue signals to digital so that the computer can process them.
| ||||||||||||||||||
| 8. | Parallel processing is sometimes used to carry out large calculations. | |||||||||||||||||
| (i) | State what is meant by the term parallel processing. | [2] | ||||||||||||||||
A
number of processors are used to carry out a task. The task is shared
between the processors.
|
||||||||||||||||||
| (ii) | Parallel processing often allows large calculations to be performed more quickly. Explain why this is the case. | [1] | ||||||||||||||||
|
Processing of the data is shared between processors which can work at the same time and
thus the task will take less time to process.
|
||||||||||||||||||
| 9(a) | Describe two advantages of an arrangement in which computers are networked, compared with standalone computers. | [2] | ||||||||||||||||
|
||||||||||||||||||
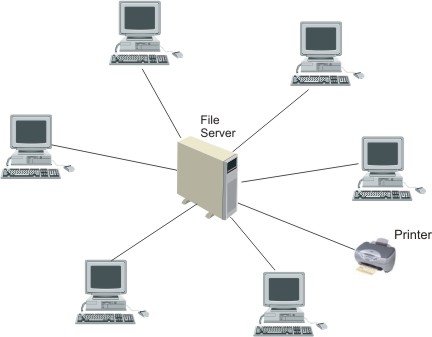
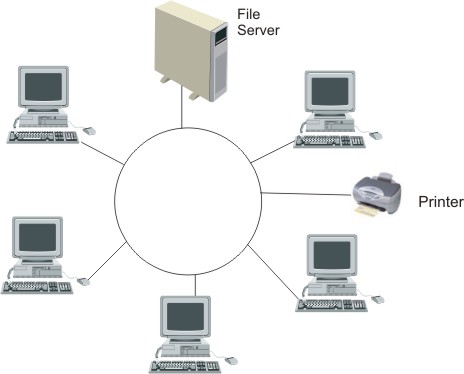
| (b) | Draw two diagrams which indicate the difference between a star network and a token ring network. | [2] | ||||||||||||||||
Star network - Each workstation is linked to a file server in the centre.
Token ring network - each computer is connected to the next one in a 'ring'
|
[1] | |||||||||||||||||
| (c) | Computer networks are very useful, but tend to be particularly prone to attack by computer hackers. Give one reason why this might be so. | [1] | ||||||||||||||||
A
user on one computer can access and change data on another computer
without anyone knowing.
|
||||||||||||||||||
| 10. | An insurance company makes extensive use of the internet and email. It also has a computer-based networked information system and its own intranet and extranet. | |||||||||||||||||
| (i) | Describe the main features of an email system. | [4] | ||||||||||||||||
|
||||||||||||||||||
| (ii) | Describe how the insurance company might use its intranet and extranet. | [2] | ||||||||||||||||
|
||||||||||||||||||
| (iii) | Some of the company's staff have access to the company's network from home. They work from home as 'teleworkers'. | |||||||||||||||||
| I | Describe one benefit to the insurance company of teleworking. | |||||||||||||||||
|
It does not have to provide office space and
facilities (canteen etc) for its workers. |
||||||||||||||||||
| II | Describe one benefit and one drawback to the employee of teleworking. | [2] | ||||||||||||||||
|
Benefit : There
is no need to commute to work.
Drawback : No contact between workers - there will be a loss of social contact. |
||||||||||||||||||
| 11. | In the following question, additional credit (up to 3 mark) will be gained if your answer demonstrates skill in written communication. | |||||||||||||||||
|
Explain in detail the term operating
system as used in a large computing system. Your answer should include a description of how a computer's operating system enables someone to use the computer and how it manages the resources of the computer. You should also include a description of both batch and real-time processing. |
[7+3] | |||||||||||||||||
|
The operating system of a computer is
a program which controls the operation of a computer. It allows a user to
input data, controls the processing of the data and organises the output
of the results.
The OS will load and run programs and data and decides where in memory to store them. It will also handle any errors which occur and inform the user of any actions which need to be taken. When data is stored on backing storage the OS will decide where to store it and change any stored tables which enable it to be found again. A batch processing system operates with no human intervention. Programs are collected in batches and the OS will load and run them automatically. A real-time system must process any input data immediately and update any data files. If a real-time system is looked at at any time it must be completely up-to-date. |
||||||||||||||||||