| [1](a) | One feature of a word processing package is a thesaurus. How could a teacher use this feature when writing end of year reports? | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | A section of a spreadsheet that a teacher uses to produce examination results is shown below with formulae being displayed. An IF function is used to determine whether a pupil has passed or failed an examination. | |||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | When the formulae are not displayed, what will appear in cell C6 and in cell C7? | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
| C6 = | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| C7 = | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Describe one other feature of a spreadsheet that the teacher could use to analyse this data. | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [2] | A school is about to equip a new computer room. The
headteacher asks the computing department to recommend either installing
twenty stand-alone computers or installing a network of twenty
computers. |
|||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | Apart from sharing hardware such as a printer, give two reasons why the department would probably recommend installing a network. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Give one reason why the department might recommend installing stand-alone computers. | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (iii) | The department recommends that spooling is used for
printing on the network. |
|||||||||||||||||||||||||||||||||||||||||||||||||
| (I) | Give two reasons why the department would recommend spooling when printing on the network. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (II) | Explain in detail how spooling is used for printing on a network. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [3](a) | What is meant by disc cache memory, and explain why disc cache memory is used. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | Disc drives use blocks when transferring data to and from disc. What is a block? | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [4](a) | Data entered into a database is often verified. Define the term data verification giving a suitable example. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (b)(i) | One method of calculating a check digit for a three digit
code is given below.
Find the check digit for the code 147. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | What is the purpose of the check digit? | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [5](a) | The personal details of members of the WellFit
gym are stored on index cards at the reception desk. Members sign a book
kept at the reception desk each time they enter the gym. Every month the
owner of the gym analyses the visitors book.
Kim is a systems analyst who recommends replacing the paper-based
system with a computerised database system. |
|||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | Describe two possible problems that could occur with the current paper-based system and explain how the new computerised database system could solve these problems. | [4] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Kim recommends a new form of data entry which requires the use of a membership card. Name a specific input device that could be used to read this card, and explain in detail how the data held on the card could be used to update the database. | [3] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (iii) | Describe one disadvantage, for the owner of the gym, of introducing this new computerised system. | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | The gym members pay by bank direct debit and their bank
and payment details are stored on the database. The owner of the gym
will have to comply with the Data Protection Act. Two of the principles
that the owner has to comply with are:
Describe three other principles with which the owner of the gym will need to comply. |
[3] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [6](a) | The mode of operation that controls an aeroplane is known as real-time processing. Describe in detail how real-time processing works in this case and explain why it is the most suitable mode of operation. | [3] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | The mode of operation that is used to book theatre tickets is known as real-time transaction processing. Describe in detail how real-time transaction processing works in this case and explain why it is the most suitable mode of operation. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [7](a) | Explain the difference between serial file organisation and sequential file organisation. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | Records within a file can be fixed length or variable length. Give one advantage of a fixed length record and one advantage of a variable length record. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
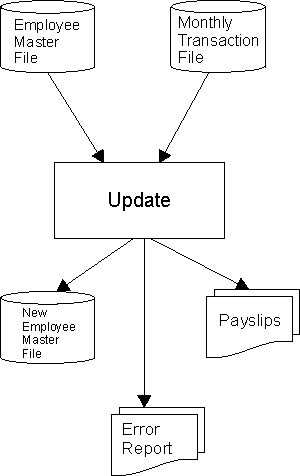
| (c) | Draw a detailed diagram that clearly shows how the master file is updated using a transaction file when a company runs the monthly payroll. | [3] | ||||||||||||||||||||||||||||||||||||||||||||||||
| [8] | A local council has its own web site, accessed via the
Internet. The council is considering setting up a staff Intranet. |
|||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | What is the difference between the Internet and an Intranet? | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Giving an example, explain what type of information the council would have on their staff Intranet but not on their Internet web site. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [9] | Explain what is meant by each of the following terms: |
|||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | address bus | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | data bus | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [10](a) | Many people now use a Personal Digital Assistant (PDA) or
a handheld computer. Often these devices are too small to have a usable
keyboard and many use handwriting recognition. |
|||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | Give one advantage and one disadvantage of using handwriting recognition as a method of input. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Describe one other suitable method of input for this type of device. | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | PDAs and handheld computers are often used to store
personal and confidential information. Some devices now have Biometric
Fingerprinting that scans the owner's fingerprints to confirm
their identity.
Describe two reasons why this method of security may be preferred to passwords. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||
| [11] | In the following question,
additional credit (up to 3 marks) will be given if your answer
demonstrates skill in written communication.
Many office employees now use computers all day and require access to the Internet and email. Some employers allow employees limited use of the Internet and email for personal use. Describe any drawbacks or benefits for the company of employees having access to the Internet and email for personal use. Describe any health concerns employers may have over employees using computers for prolonged periods. Explain any preventative measures that could be implemented to reduce these risks. |
[7+3] | ||||||||||||||||||||||||||||||||||||||||||||||||
If employees can access the Internet, they can use
it to research any problems they may be having or access forums to see if
others have suggestions or solutions. There may also be problems with
users wasting too much time on recreational or inappropriate sites, such
as gambling or pornography sites, when they should be working. Shopping
sites may also be too tempting.
With access to emails, employees can request assistance from others and receive fast responses, but there may also be a problem of spreading viruses around the office network. Sitting for long periods at a computer can cause some health problems such as RSI (Repetitive Strain Injury), back or neck problems or eye strain. The best way of preventing these problems is to have suitably arranged desks and chairs, and to make sure that the employees have frequent breaks. The lighting in the office should also be considered - if the lighting is too bright it may result in eye strain.
|
||||||||||||||||||||||||||||||||||||||||||||||||||