| [1](a) | A teacher uses a word processor to produce cards with a
picture on one side and large text on the other side describing the
picture. Describe two features of a word processing package that would be essential in producing these cards. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | The teacher also uses the spreadsheet below to manage her
classroom expenditure. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | Write down the formula that should be contained in cell B9
to calculate the total expenditure to date and the formula that should
be contained in cell B13 to
calculate the amount still available. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Write down the formula that should be contained in cell B15
to display 'YES' or 'NO' depending on whether an overspend has occurred
or not. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
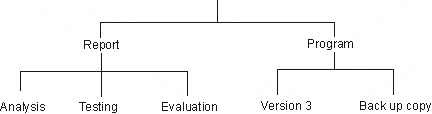
| [2](a) | A computing student has organised the storage of his files
on a hard disc, as shown in the diagram below. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | What name is given to this type of file structure? |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Explain why this is a sensible way of organising file
storage. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | One attribute a file may have
is read only; state one
other attribute a file may have. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (c) | Disc drives use blocks when
transferring data to and from disc. What is a block? |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [3](a) | Explain the difference between data validation and data verification. | [2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | Validation and verification checks are carried out on data
being entered into a database at a video rental shop. One item of data
to be entered is:
Describe a suitable validation check
that could be carried out on the number of films
in stock, and give an example of invalid
data that would be detected by this validation
check. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Description of the validation
check |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Example of invalid data |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (c) | Employees at the shop log in using a password. Employees'
passwords are changed on a regular basis. Describe a suitable verification
check that should be carried out when an employee changes their
password. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Description of the verification
check |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Describe what happens if verification
fails |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [4] | The file server of a small business has a large hard disc
that needs to be backed up. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | Name a secondary storage device that would be suitable for
making a back up of a large hard disc. Describe a suitable strategy for
backing up this data. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Describe how the secondary storage device should be stored
and how this may then be used to restore the data after a fire has
completely destroyed the server. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [5](a) | Using an example in each
case, explain the meaning of the following terms: |
[6] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Field |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Record |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| File |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | Explain how a record is added to: |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | a serial file |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | a sequential file |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [6](a) | Using a suitable example, explain the computer term bit. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | Using a suitable example, explain the computer term byte. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (c) | Explain the computer term word. | [1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [7](a) | Describe three examples of
how an operating system manages resources. |
[3] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (b)(i) | Explain how spooling is
carried out on a computer when several documents need to be printed. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Describe a benefit of spooling
for the user. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (c) | Explain the term time slice
when used in a multi-user operating system. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [8] | Some hand held devices use voice input commands to operate
the device. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | Why is voice input a suitable method of input? |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | Describe two situations where
commands may not be recognised by the device. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (iii) | How could the device be operated when the voice input does
not recognise a command? |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [9] | A local council stores data on residents. The data
includes names, addresses and the value of their houses. Employees
access the council's computer system using usernames and passwords and
have access to residents' data. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (a) | The council suspects that some staff are benefiting
illegally from having access to residents' data. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (i) | Describe how a council employee could illegally benefit
from having access to the residents' data. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (ii) | All employees are required to comply with the council's
code of conduct. Explain how this code of conduct may reduce such
illegal activity. |
[1] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (iii) | Apart from passwords and a code of conduct, describe two
other measures that the council might adopt to try and prevent employees
taking part in such illegal activities. |
[2] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| (b) | The council complies with the Data Protection Act by
ensuring that residents' data is obtained lawfully, held securely and
held for no longer than necessary. Describe three
other ways in which the council must operate in order to comply with the
Data Protection Act. |
[3] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| [10] | A mother, father and two children have three computers in
their house. The computer in the study is used by the parents to help
with their business and has Internet access and email. This computer has
a printer and a scanner attached.
The children have a stand-alone computer in each of their bedrooms that they use for school homework and to play games. When the children want to access the Internet or print or scan a document they use the computer in the study. The children have suggested networking all three computers. Describe the benefits and drawbacks of this home-based network. The children sometimes spend long periods on the computer. What
effect might this have on their health? |
[9+3] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
If
the computers are networked, the hardware such as the scanner and
printer can be shared and used by any computer on the network, so the
children could print their homework directly. It would also be
possible for the children to use the Internet access for research for
their homework, and send emails. Instant messages could also be sent
from one computer to another in the house.
The Internet access for the children would have to be controlled so they do not access undesirable sites such as pornography or unrecognised chat rooms. There may also be a potential for viruses to attack all the computers in the house, so virus-protection software would need to be installed. There may also be a danger of the children hacking into the parents' business files, and accidentally deleting data. If children spend too much time on the computer, their level of fitness is going to deteriorate, and this may lead to obesity and other medical problems. There may also be problems with loss of social skills if the children do not go out and mix with others. Other problems associated with extended computer use are back or neck strains, eye strain or RSI.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||