| [1] | State, giving a reason in each case, the most suitable secondary storage medium for each of the following situations. | |
| (i) | Making a backup copy of a school's file server (200 Gigabytes) | [2] |
|
||
| (ii) | A school pupil submitting course work to an examination board that contains text, graphics and video (600 Megabytes). | [1] |
|
||
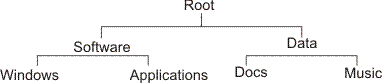
| [2](a) | Files on the hard drive of a personal computer are stored
in a hierarchical directory structure.
Using a diagram, show how files might be organised in a typical
hierarchical directory structure used on a
personal computer.
|
[1] |
|
||
| (b) | Explain why this type of structure is used. | [1] |
|
||
| [3] | A firm of solicitors using a number of stand-alone personal computers decide to update their computer system. They employ a consultant who recommends that they install a network. | |
| (i) | Apart from sharing hardware such as a printer, give two reasons why the consultant would probably recommend installing a network. | [2] |
|
||
| (ii) | Give one reason why the consultant might recommend keeping some stand-alone computers. | [1] |
|
||
| (iii) | The consultant recommends networking the computers using a star network topology. Draw a diagram that illustrates this topology. | [1] |
|
||
| (iv) | Give one advantage and
one disadvantage of using a star network
topology rather than other topologies.
|
[2] |
|
||
| [4] | Students enrolling on a college course are asked to
provide personal details: these include their
postcode and number of GCSE subjects for
which they have achieved grades A*-C, which should be an integer.
These details are entered into the college computer system. Describe suitable validation checks that could be carried out on this data and give an example of invalid data that would be detected by the check described. A different validation check must be used in each case.
|
[4] |
|
||
| [5] | Sun All Year is a tanning studio. Client details are
collected during their first visit and these details are stored on paper
in files at reception. The number of clients is growing and the studio owner believes that storing the client details on a new computerised database system could improve the business. The studio has found that contacting clients using the paper-based system is extremely time consuming.
|
|
| (i) | Describe one other possible problem with the current
paper-based system that may lead to the studio losing business. Describe
how a computerised database system could solve
this problem.
|
[2] |
|
||
| (ii) | Describe two ways in which the studio could use a
computerised database system containing the client details to attempt to
increase the number of visits from clients.
|
[2] |
|
||
| [6](a) | The operating system of a computer provides an interface
between the hardware and the user. Describe three
typical functions of the operating system from the user's point of view.
|
[3] |
|
||
| (b)(i) | A gas company uses batch processing
to produce quarterly bills. Describe how batch
processing works in this case and explain
why it is the most suitable mode of operation.
|
[2] |
|
||
| (ii) | A nuclear power station uses
real-time processing to control reactor temperature. Describe
in detail how
real-time processing works in this case and explain
why it is the most suitable mode of
operation.
|
[3] |
|
||
| [7] | A holiday company specialises in adventure ski holidays.
The company has thousands of customer records which are stored on a
computer. These records include information about customer financial
status. The manager of the company is concerned about computer crime and believes that some computing staff may be benefiting illegally from their position.
|
|
| (i) | Describe one way in which a dishonest employee with access to customer records could illegally benefit from their position in the company. | [1] |
|
||
| (ii) | All company employees are asked to comply with the company code of conduct. Describe one effect a code of conduct may have on the behaviour of employees. | [1] |
|
||
| (iii) | Security systems introduced by the company include the use
of usernames and passwords. Describe two
other measures that could be adopted to prevent its computer staff
illegally benefiting from their position in the company.
|
[2] |
|
||
| (iv) | The company has registered with the Data Protection
Commissioner. The company complies with two principles of the Data
Protection Act by processing the data lawfully and storing the data
securely. State three other principles of
the Data Protection Act with which the company will need to comply.
|
[3] |
|
||
| [8](a) | Explain the difference between serial file organisation and sequential file organisation. | [2] |
|
||
| (b) | Records can be fixed length or variable length. Give one advantage of a fixed length record and one advantage of a variable length record. | [2] |
|
||
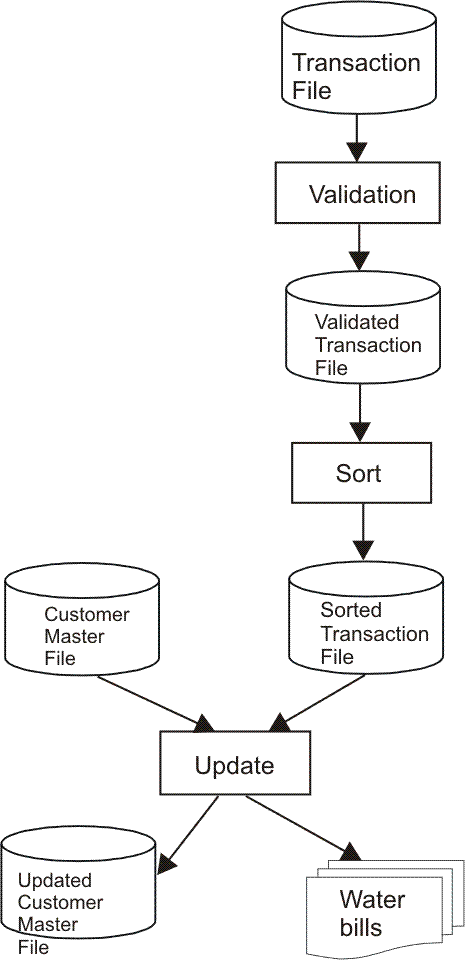
| (c)(i) | A water company sends bills out to every customer. Draw a
detailed diagram that clearly shows how the
master file and the
transaction file are used to produce the bills.
|
[4] |
|
||
| (ii) | When bills are produced, several items of data are updated in the master file. State one data item that is updated. | [1] |
|
||
| [9](a) | What is the computer term for the number of bits that can be processed as a single unit by the CPU? | [1] |
|
||
| (b) | A computer often has to exchange signals with a peripheral device to establish their readiness to send or receive data. What is this communication called? | [1] |
|
||
| (c) | Hardware and associated software is required for communication to take place between the processor and a peripheral. What is the name given to the hardware? | [1] |
|
||
| [10](a) | Explain, using a diagram, how four parallel processors P1, P2, P3 and P4 could be used to find the total of eight numbers 3, 7, 5, 8, 2, 9, 1 and 6. | [2] |
|
||
| (b) | Give one advantage of using parallel processing rather than a single processor. | [1] |
|
||
| [11]. | In the following question,
additional credit (up to 3 marks) will be gained if your answer
demonstrates skill in written communication. A parcel delivery company has many drivers delivering parcels. The parcels are loaded on a van in the morning in the order required for the delivery route. Every parcel has a delivery note that contains all the delivery details and has space for the customer's signature. The company office frequently needs to contact the drivers to give new delivery instructions. The driver often has to contact the office for alternative routes to avoid congestion and to give reasons for failed deliveries. This communication is currently made using mobile telephones. The company decides to replace the driver's mobile telephone and paper delivery notes with a new hand held computing/communication device. Describe what functions this hand held device could carry out. Describe what methods of input would be most suitable to perform the functions described.
|
[7+3] |
|
||
 xx
xx