| [1] | A secretary in a solicitor's office uses a word processor to write reports and letters. Two features regularly used are print preview and the thesaurus. | |
| (a) | Briefly describe the print preview feature and give an example of how it could be useful to the secretary. | [2] |
|
||
| (b) | Briefly describe the thesaurus feature and give an example of how it could be useful to the secretary. | [2] |
|
||
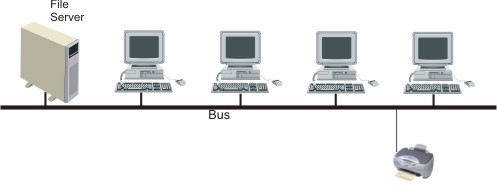
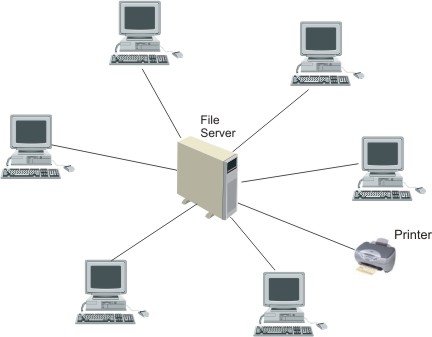
| [2](a) | Draw two diagrams that show the difference between a bus network and a star network. | [2] |
|
|
||
| (b) | Give two advantages of using a star network rather than a bus network. | [2] |
|
||
| (c) | Describe a situation where it would be preferable to have several standalone computers instead of having computers networked. | [1] |
|
||
| [3] | State, giving a reason in each case, the most suitable secondary storage medium for each of the following situations. | |
| (a) | Making a back up copy of the complete hard disc drive of a computer used in a small business (250 Gigabytes). | [2] |
|
||
| (b) | Sending copies of many high resolution photographs, in electronic form, to a family friend through the post (4 Gigabytes) | [2] |
|
||
| (c) | A manager taking a computer presentation home, in electronic form, from the office (3 Megabytes). | [2] |
|
||
| [4] | Staff working for a large company use computers every day. Describe three ways in which the prolonged use of computers might affect the health of the staff. | [3] |
|
||
| [5] | Employees in an organisation each have a unique employee code made up of two letters, two digits and two letters, for instance PY45FT. A validation check is applied to the employee code. | |
| (a) | What is the purpose of validation? | [1] |
|
||
| (b) | Describe two types of validation check which might be applied to this employee code giving an example of invalid data detected by the check in each case. | [4] |
| First validation check | ||
|
||
| Example of invalid data detected by this check | ||
|
||
| Second validation check | ||
|
||
| Example of invalid data detected by this check | ||
|
||
| [6](a) | Give three reasons why voice recognition is not yet in widespread use as an input method for personal computers. | [3] |
|
||
| (b) | Describe two advantages of voice recognition as an input method compared with keyboard input. | [2] |
|
||
| [7](a) | Explain how a record is added to: | |
| (i) | a serial file | [1] |
|
||
| (ii) | a sequential file | [2] |
|
||
| (b) | Records within a file can be fixed or variable length. | |
| (i) | Give one advantage of a fixed length record. | [1] |
|
||
| (ii) | Give one advantage of a variable length record. | [1] |
|
||
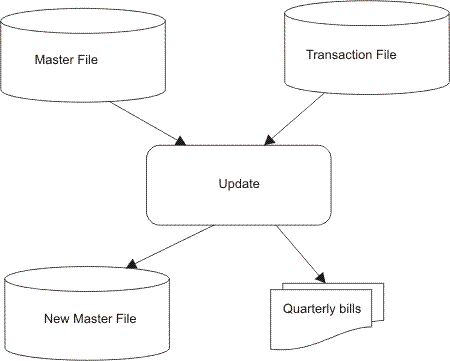
| (c) | Draw a detailed diagram that clearly shows how the master file is updated using a transaction file when an electricity company produces quarterly bills. | [4] |
|
|
||
| [8](a) | Describe three typical functions of the operating system from the user's point of view. | [3] |
|
||
| (b)(i) | Explain how spooling is carried out on a computer when several documents need to be printed. | [2] |
|
||
| (ii) | Describe a benefit of spooling for the user. | [1] |
|
||
| [9] | A certain computer uses a word length of 32 bits. | |
| (a) | Define the term word in this context. | [1] |
|
||
| (b) | An advantage of using a long word length is that the computer may work faster. Briefly describe why this is the case. | [1] |
|
||
| [10] | A company stores personal data about customers. Company employees have access to this data. Employees are required to comply with the company's code of conduct and have usernames and passwords to access the data. | |
| (a) | Apart from passwords and a code of conduct, describe two other measures that the company might adopt to try to prevent employees benefiting illegally from having access to this data. | [2] |
|
||
| (b) | The company complies with the Data Protection Act by ensuring that the data is obtained lawfully, held securely and is not kept longer than necessary. Describe three other ways in which the company must operate in order to comply with the Data Protection Act. | [3] |
|
||
| [11] | In the following question,
additional credit (up to 3 marks) will be given if your answer
demonstrates skill in written communication.
|
|
| CymruSpa is a thriving hotel
set in rural Wales. They offer several different types of room such as
standard twin or luxury suites and different meal options such as bed
and breakfast or full board. They cater for all types of eating
preferences and special dietary requirements such as wheat intolerance. The hotel has decided to computerise their current paper-based data storage system which contains details of bookings and of all guests who have stayed at the hotel. Apart from personal details such as name and address, describe relevant items of data that should be stored in the new system. The hotel has decided to use a database system. Explain any improvements this new database system will have over the current paper-based system. |
[7+3] | |
The new database will allow faster access to the data so the hotel management can speedily produce reports such as a list of guests arriving on a particular day. They will also be able to query the database to produce, for example, lists of rooms that are still available on a particular date. This could be done very quickly when an enquiry is made. There will be no need for large and complex storage systems for paper, and less time will be needed for filing documents.
|
||