| [1] | When developing a new computer system, programmers sometimes use a software package rather than a traditional programming language. | ||||||||||
| (i) | Describe two possible benefits of this package-based approach compared with the use of a programming language. | [2] | |||||||||
|
|||||||||||
| (ii) | Describe one possible drawback of this package-based approach compared with the use of a programming language. | [1] | |||||||||
|
|||||||||||
| [2](i) | Explain, using a diagram, the term stack as used in a computer system. | [2] | |||||||||
|
|||||||||||
| (ii) | Explain what should happen when an attempt is made to add an item to a full stack. | [1] | |||||||||
|
|||||||||||
| (iii) | Describe a computer application which would normally use a
stack. Why is a stack appropriate in this case? |
[2] | |||||||||
|
|||||||||||
| [3](a) | Handwriting recognition is increasingly used as a form of human computer interface (HCI). | ||||||||||
| (i) | Describe two possible benefits of this type of HCI compared with keyboard input. | [2] | |||||||||
|
|||||||||||
| (ii) | Describe two possible drawbacks of this type of HCI compared with keyboard input. | [2] | |||||||||
|
|||||||||||
| (b) | Describe how the design of an HCI should be evaluated. | [1] | |||||||||
|
|||||||||||
| [4](a) | What term is used to describe a group of related data items? | [1] | |||||||||
|
|||||||||||
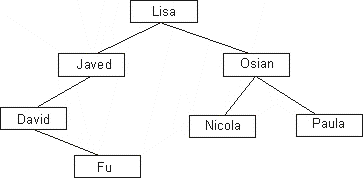
| (b) | The following binary tree has been produced by inserting
the names. Lisa, Osian, Nicola, Javed, David, Fu and Paula, in that order. In each case, the right pointer indicates the condition: later on in the alphabet |
||||||||||
|
|
|||||||||||
| (i) | Write down the name contained in the root node. | [1] | |||||||||
|
|||||||||||
| (ii) | Write down the order in which the nodes would be accessed to reach the name Nicola. | [1] | |||||||||
|
|||||||||||
| (iii) | The name Ed is not in the above diagram. Explain the steps that would take place if a search was made for this name. | [1] | |||||||||
|
|||||||||||
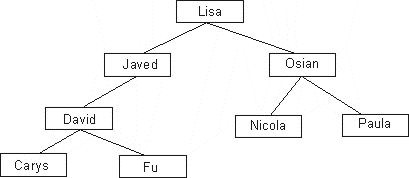
| (iv) | Copy the diagram then add the name Carys
in the correct place on the diagram. (You may use just the initial letter of all names if you wish). |
[1] | |||||||||
|
|||||||||||
| (v) | This tree diagram is reasonably well balanced in shape. What would happen to access times if the tree was much less well balanced? | [1] | |||||||||
|
|||||||||||
| [5](a) | Using eight bits and two's complement form, convert the number -910 to binary. | [1] | |||||||||
|
|||||||||||
| (b) | Computer systems often truncate numbers. Explain the term truncate giving an example. | [2] | |||||||||
|
|||||||||||
| (c) | In many computers, characters are stored using a standard code. | ||||||||||
| (i) | In one standard code, the character "4" is stored as 0110100. The character "5" is stored as the next higher binary code (0110101) and so on. How will the character "8" be stored? | [1] | |||||||||
|
|||||||||||
| (ii) | What is the advantage of using a standard code of this type? | [1] | |||||||||
|
|||||||||||
| (d) | Write down the effect of carrying out an arithmetic shift left by three places on the positive integer 00001010 | [1] | |||||||||
|
|||||||||||
| Explain the effect of this operation on the number. | [1] | ||||||||||
|
|||||||||||
| [6](a) | Explain what is meant by the term algorithm. | [2] | |||||||||
|
|||||||||||
| (b)(i) | Describe two features of a recursive algorithm. | [2] | |||||||||
|
|||||||||||
| (ii) | Describe one advantage of a recursive algorithm. | [1] | |||||||||
|
|||||||||||
| (iii) | Give one example of a recursive algorithm. | [1] | |||||||||
|
|||||||||||
| [7](a) | Write down the truth table for: | ||||||||||
| (i) | the AND operation | [2] | |||||||||
|
|||||||||||
| (ii) | the EXCLUSIVE OR (XOR) operation. | [2] | |||||||||
|
|||||||||||
| (b)(i) | Carry out the XOR
operation on the following:
A = 10001101 K = 10101111 |
[2] | |||||||||
|
|||||||||||
| (ii) | State what the results would be if you carried out a XOR on your answer to part (b)(i) and the number K. | [1] | |||||||||
|
|||||||||||
| (iii) | State a security application which this operation might be used for. | [1] | |||||||||
|
|||||||||||
| [8](a)(i) | Describe the difference between a compiler and an interpreter. | [2] | |||||||||
|
|||||||||||
| (ii) | Describe the lexical analysis stage of compilation, ensuring you make the output of this stage clear. | [2] | |||||||||
|
|||||||||||
| (iii) | Describe the semantic analysis stage of compilation. | [2] | |||||||||
|
|||||||||||
| (b) | Explain the term relocatable code. | [1] | |||||||||
|
|||||||||||
| (c) | A debugging tool contains a program
trace facility and a store dump
facility. Explain each of the two terms: |
||||||||||
| (i) | a program trace facility | [1] | |||||||||
|
|||||||||||
| (ii) | a store dump facility. | [1] | |||||||||
|
|||||||||||
| [9] (a) | What is the purpose of Backus Naur Form (BNF)? | [1] | |||||||||
|
|||||||||||
| (b) | One way of defining a decimal number is:
For instance, the following are covered by this definition: +23.5 23.5 -0.5 0.0 +0.728 Produce an appropriate BNF definition for a decimal number as defined above. |
[4] | |||||||||
|
|||||||||||
| [10] | Marks obtained by candidates in an examination are
terminated with a rogue value of -99.
An example of a set of examination marks (including the rogue value) is shown below, 62 71 48 35 76 61 54 38 52 -99 For this particular examination:
Design an algorithm which will read in a set of marks of this type and will output the number of candidates being given each of the three grades. |
[4] | |||||||||
DistinctionCounter=0 PassCounter=0 FailCounter=0 repeat input(ExamMark) if (ExamMark <> -99) then if (ExamMark >= 70) then DistinctionCounter = DistinctionCounter+1 if (ExamMark >=40) and (ExamMark <= 69) then PassCounter = PassCounter + 1 if (ExamMark < 40) then FailCounter = FailCounter + 1 end if until (ExamMark = -99) output(DistinctionCounter) output(PassCounter) output(FailCounter) |
|||||||||||
| [11] | In the following question,
additional credit (up to 3 marks) will be gained if your answer
demonstrates skill in written communication.
A programmer is developing a set of programs and needs to make a number of decisions. One decision relates to the human computer interface (HCI), and whether this should:
Another decision is the type of programming language to be used, for instance whether to use:
Describe in detail the features of the different HCI types in the first list which might influence the choice of HCI type. Also describe in detail the features of the different programming languages in the second list which might influence the choice of language. |
[9+3] | |||||||||
A graphical user interface (GUI) would use icons to
represent applications which would be selected by clicking a mouse
pointer on them. This would be an instinctive, easy to use interface
suitable for users with low IT skills. This type of interface would
however use a lot of computer resource such as memory.
A text-based interface would use less memory and operate faster, but would only be suitable for expert users as the commands need to be learned. Speech recognition systems are useful for situations where the user is either handicapped or unable to use their hands such as a fighter pilot or surgeon. There may be problems with recognising some people's voices due to regional accents or voice problems such as heavy colds. Speech synthesis allows the user to continue with their task such as driving a car, without needing to look at a monitor screen, and it is also useful for those with a visual handicap. Visual programming languages allow programmers to create programs quickly without much coding. Useful for developing applications in a WIMP environment. Fourth generation languages have many powerful built-in features such as searching and sorting so program coding is less burdensome. Object oriented languages use objects that have properties and methods. Each object reacts to certain events (such as clicking the mouse) according to subroutines (event handlers) written by the programmer. These are useful for event-driven programs.
|
|||||||||||