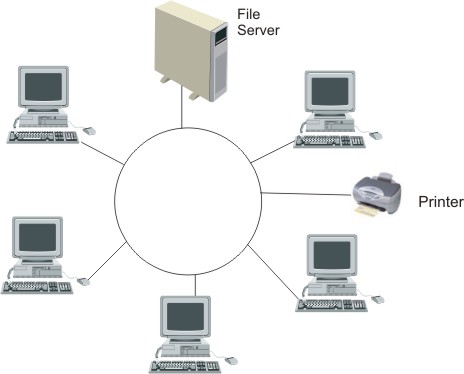
| 1(a) | Computer systems are used in most supermarkets to run the stock control system. | |
| (i) | Describe in detail why computer systems are useful in this context. | [5] |
|
(make sure you have at least five different points)
|
|
| (ii) | Describe two ways in which computing developments in the last two decades have favoured this type of application. | [2] |
|
||
| (b) | Most stock control systems use databases. | |
| (i) | One advantage of using a database rather than a traditional file system is that it reduces data duplication. Give two reasons why data duplication is undesirable. | [2] |
|
||
| (ii) | Database applications can be more secure than traditional file systems. Give two reasons why this is the case. | [2] |
|
||
| 2. | A new light railway system is to use driverless trains. A computer system will control the movement of trains between stations and will include comprehensive safety systems. For instance, the trains will not move if any door is open and will stop if an obstruction is sensed on the line ahead. | |
| (i) | State two inputs which will be required to the control system of the train. | [1] |
|
||
| (ii) | Describe two outputs which will be required from the control system of the train. | [2] |
|
||
| 3. | Explain the terms: | |
| (i) | serial file organisation; | |
|
||
| (i) | sequential file organisation; | |
|
||
| (b) | Explain the difference between fixed length and variable length records. State one advantage of each type of record. | |
|
||
| 4(a) | Modern word processors contain many features. State the function of each of the following features. giving an example of its use in each case. | |
| (i) | thesaurus | [2] |
|
||
| (ii) | header/footer | [2] |
|
||
| (b) | A criticism of word processing systems is that they often result in paper being wasted. Explain why this may happen. | [1] |
|
||
| (c) | A spreadsheet is used to calculate the wages of the employees in a small company. | |
| (i) | Describe two features of a spreadsheet which make it useful in this application. | [2] |
|
||
| (ii) | Most spreadsheet packages contain a macro feature. Explain the term macro, giving an example from the wages application. | [2] |
|
||
| (d) | Apart from job losses which may result from the use of word processing and spreadsheet facilities, state two areas of employment which have been considerably affected by the widespread use of these facilities, and explain how each has been affected. | [2] |
|
||
| 5.(a) (i) |
Describe two important features of an operating system in a personal computer. | [2] |
|
||
| (ii) | Describe two additional features which the operating system of a mainframe computer might include, which would not normally be found on a personal computer. | [2] |
|
||
| (b) | Explain the term on-line processing. | |
|
||
| (c) | The phrase real-time
processing can apply to two quite different computing environments.
An example of the first environment is a real-time airline booking system. An example of the second environment is a real-time control system used to fly the aircraft. Explain the term real-time processing, making clear the difference between these two environments. |
[2] |
|
||
| (d) | Give a detailed explanation of the term handshaking when used in connection with computer input or output devices. Give an example of handshaking as applied to the use of a printer. | [5] |
|
||
| 6.(a) | Two computer workers, Matthew and Vicky, are
discussing data security.
"I always keep really valuable data on the hard disc of my personal computer," says Matthew. "I wouldn't keep it on a floppy disc." "I don't agree at all," replies Vicky. "I only ever keep valuable data on a floppy disc - I certainly wouldn't keep it on a hard disc." Describe how each of these points of view can be justified: |
|
| (i) | Matthew's point of view; | [1] |
|
||
| (ii) | Vicky's point of view | [1] |
|
||
| During this conversation, Rhiannon joins the other two, saying "Whichever you choose, it's always sensible to keep a paper back-up." | ||
| (iii) | Justify Rhiannon's viewpoint. | [1] |
|
||
| (b) | Optical storage devices which can be written to (usually known as writable CD-ROM drives) are increasingly available for storing valuable data. State one potential advantage and one potential disadvantage of this method compared with other methods named above. | [2] |
|
||
| 7(a) | Describe two advantages of an arrangement in which computers are networked, compared with standalone computers. | [2] |
|
||
| (b) | Describe one possible disadvantage of networking computers. | [1] |
|
||
| (c)(i) | Draw two diagrams which indicate the difference between a star network and a token ring network. | [1] |
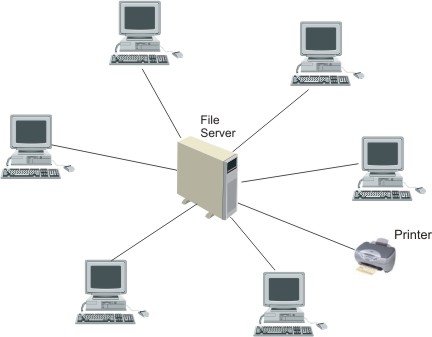
|
||
| (ii) | Describe the operation of a star network. | [1] |
|
||
| (d) | Describe the operation of a token ring network. | [3] |
|
||
| (d) | State the difference between a WAN (wide area network) and a LAN (local area network) | [1] |
|
||
| (e) | Many networks have some type of security system to prevent inappropriate access. Passwords are often used as a security measure to try to prevent unauthorised access. Describe three ways in which a password system can be made as secure as possible. | [3] |
|
||
| 8(a) | State the meaning of the following two terms: | |
| (i) | the internet; | [1] |
|
||
| (ii) | an intranet. | [1] |
|
||
| In the following part-question, additional credit will be gained if your answer demonstrates skill in written communication. | ||
| (b) | The internet can also be used to help people
taking college courses. Course notes and examples are made available via
the internet and students can communicate with their tutors via the
internet. In addition to taking part in "distance learning", the
students are able to use the internet for leisure and entertainmnt.
Describe possible benefits and drawbacks of this distance learning arrangement ( to both students and staff) compared with a conventional course involving student attendance at the college. Also discuss the concern that many people have over the leisure use of the internet by young people. |
[8] |
|
Staff and students will need to spend less time
travelling. This is particularly important in a rural area, where they
may live far from the college. There are educational advantages too, for
instance, students may engage in on-screen discussion with other
students and with staff. Course materials (including additional work for
able students or remedial work for less able students) may be published
electronically, thus saving paper. However the reduced face-to-face
contact with both staff and students may hamper student progress.
Many people are very concerned over easy access of young (and older) people to pornography, or material related to illegal drugs or other criminal information. There is also a concern about time-wasting, and that some people may suffer socially (and possibly physically) from spending too long in front of a computer screen. One of the major problems is that it is very difficult for governments to control access to the internet. |
||