|
Files used in applications are vital to the
running of a system. Any loss or corruption of data will have
serious or fatal implications for the performance of the
application. Delays, loss of business and possible legal action
may result. For these reasons many safeguards are used to protect
files from:
- Hardware failures - all hardware
dies eventually.
- Software failures - programming bugs
can be hidden for a long time before a rare combination of events reveals
the problem.
- Human Errors - Accidental
changing of data or deletion of files.
- Deliberate damage - may be caused
by an angry employee, a virus or a hacker.
Physical Security
- Security guards
- Alarm systems
- Locks on rooms and on computers
- Access to rooms by swipe cards / fingerprint scan / retina scan
- Write-protect mechanisms - some
drives and memory sticks have write-protect tabs. When switched on, the
changing of data is impossible.
Passwords - Levels of permitted access
In
order to gain access to the system a user is supplied with a user
name together with a personal password.
The operating system will check the user
name and password are valid before allowing the user to log in.
Some files may be
open by anyone, others only by those users with a particular
level of access. It is possible that some
levels of access allow a user to read but not change the data. The main computer's operating system makes sure that file access is appropriate for the
user's password.
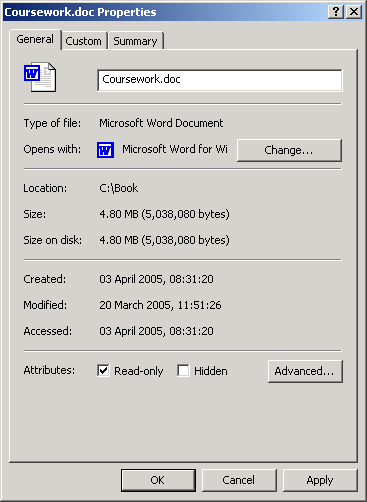
File Attributes
The file itself has attributes that can
be set. The commonly used ones in Windows are:
- Read-only
- the file can be read but not altered
- Hidden
- the file is not displayed in listings of files.
Firewalls
Computers connected to networks - especially the Internet - need to be
protected from hackers. Firewalls are
software methods of blocking access to anyone from outside a network unless they
are authorised.
|